Vulnerability Management
Companies need to be well prepared in order to combat the ever-evolving threats posed by cyberattacks. Or do you know exactly which of your systems are most vulnerable?
Vulnerability management allows you to keep a watchful eye on your IT infrastructure, ensuring early detection of potential vulnerabilities and helping minimize risks. On this basis, you can switch your IT security strategy from a reactive to a proactive approach.
Continuous monitoring for a better overview
Vulnerabilities have to be identified, assessed and remedied correctly and in good time to help you update and protect vulnerable systems at the earliest possible stage. Continuous monitoring and vulnerability management reduce the costs of IT operations in the long term.
Your benefits:
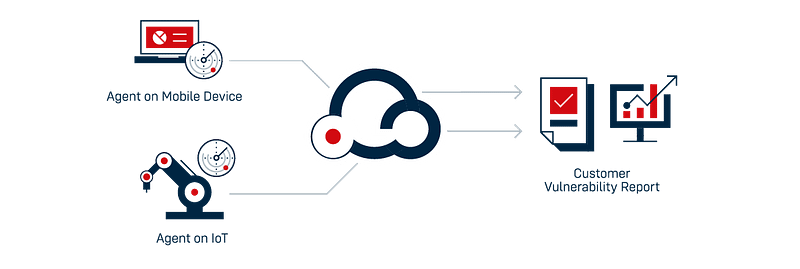
- On-premises and cloud scan, passive scanners (IIoT)
- Agents for mobile devices, machines, public clouds and managed devices
- Monitoring via API for cloud services
- Reporting
Want to learn more about vulnerability management? Then don’t hesitate to get in touch with us. Our experts will be happy to assist you with this basic concept.
Want to learn more about application web security? Then get in touch with us. Our experts are here to support you in every aspect.
